TLDR: Threat modeling comes in a variety of approaches. Knowing what you are trying to protect can help steer you to a more appropriate method.
Unless you are vehemently against technology, you have used it at some point in your life. Perhaps you have a cell phone, a laptop computer, or, for most of us, have used a debit or credit card. Our lives, the organizations we work for, and the businesses we patronize all thrive on technology. With the explosion of technology to help make life easier for civilization, it is also imperative for us to continually remember there are those out there who want to inflict harm. This is where threat modeling can help an organization protect itself and, to some degree, individuals as well.
In his book, Threat Modeling: Designing for Security, Adam Shostack provides three primary approaches to threat modeling: asset, attacker, and software. Each of these three methods focuses on different areas of threats and how to mitigate, eliminate, transfer, or accept the associated risks. Now, it is certainly not feasible that individuals would perform construct a threat model for each new technology they add to their pocket or household, but some of these things should come to mind. Organizations, on the other hand, must perform threat modeling for each asset and system added to the inventory. While each model has its pros and cons, it may really come down to a mixture of all three approaches. Let’s look at each to see why that might be the case.
Asset-centric threat modeling means putting emphasis on what you value and then looking at the vulnerabilities associated with those assets. From a personal perspective, this could be looking at what threats you have to accessing your bank account information online. Can your password be stolen and used to long into the banking application? From an organizational perspective, this could be protecting a database full of client records. What threats exists to this data and how can we further protect it? The focus here is on what one values.
Attacker-centric threat modeling focuses on what an attacker might do. Instead of looking at assets to protect, this approach looks at the various tactics and techniques an attacker might use to attempt to gain access to an asset. If you think like a burglar when looking to protect your home, you might install a second lock on the door or find better ways to secure your windows. On the organizational side, this can include things like focusing on a list of usernames and passwords for critical systems. Perhaps you want to check these credentials to make sure they cannot be easily cracked. Again, the thought here is to consider, “what would an attacker do?”
The last threat modeling approach Shostack discusses is that of a software-centric approach. This approach is focused on dealing with software and systems being deployed within an organization. On the personal side, you can think of this as installing software on your laptop or even your smartphone. You certainly do not want to install anything which would let someone have access to your personal information. Likewise, organizations need to use this approach to look for holes which may allow attackers to gain access to their assets. If software is being deployed within the organization, are there concerns which may open up vulnerabilities on the computers or networks critical to the organization’s operations? These are things to consider when using a software-centric approach to threat modeling.
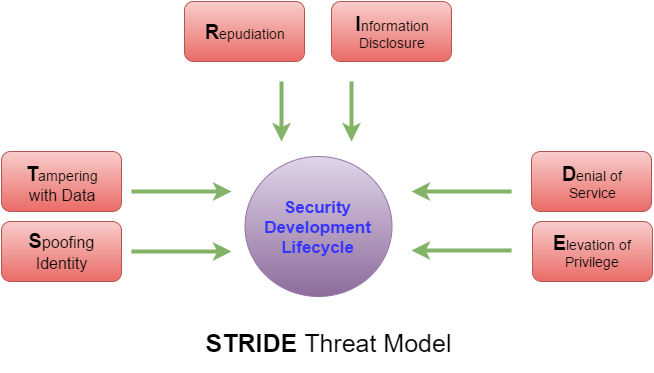
Another threat modeling approach is STRIDE. STRIDE stands for spoofing identity, tampering with data, repudiation, information disclosure, denial of service, and elevation of privilege. This approach really pertains mostly to information systems but can be thought of with other threats as well.
Shevchenko points out that this approach was invented in 1999 and adopted by Microsoft in 2002. Knowing that this applies primarily to information systems (IS) helps to see why Microsoft adopted this approach to threat modeling.
Spoofing an identity, in the IS world, concerns the authentication of systems or the authenticity of packets on a network. Someone can steal your credentials, log into a computer system, and pretend to be you while they perform malicious actions. Similarly, a hacker can spoof the identity of a packet, launching a man-in-the-middle attack, and pretend to be the sender or receiver of information. In the physical world, this would be similar to someone posing as a repair person or a delivery driver to gain access to a building.
Tampering with data concerns the integrity of data within a system. This can be data at rest on a computer disk or memory as well as data moving through a network. A student finding their grades stored on the school’s computer network and modifying them to earn an A in all of their classes would be an example of tampering with data at rest. A hacker taking a packet of information, modifying it to change values, and sending it onto the destination is an example of modifying moving data.
Repudiation pertains to validity of actions. If repudiation is present, one can deny the actions were taken on their part. For instance, if a critical file was modified or deleted, who was responsible for it? The violation of non-repudiation means there is no way to confirm or deny that a specific entity was responsible for accomplishing actions. From a physical standpoint, this would be like a sign-in sheet to a class. If you signed in, it is generally accepted you were there. In the absence of a sign-in sheet, it becomes more difficult to determine if you did or did not attend the class. This is something commonly handled through the use of log files to document all actions and who took those actions.
Information disclosure concerns information getting into the hands of someone it is not supposed to. For an IS, this could include incorrect folder permissions allowing someone to modify financial records in the accounting division when they should not have access to such documents. In the physical world, someone gaining access to an unlocked filing cabinet and pulling personnel records when they do not have a need to know falls into the same category. Information which should be safeguarded is compromised due to a lapse in confidentiality.
When talking about denial of service, this typically means that an IS is unavailable when needed. You have likely heard of DDoS attacks where attackers create an army of zombie computers to bring a web server down. They bombard the server with so many requests that the server cannot keep up and eventually access is denied to users who need to use it. The bombardment of bogus requests causes any relevant requests to be ignored by the system. You could liken this to a need to reach a 911 operator when thousands of pranksters are calling in to keep the phone lines busy. You have a legitimate need but cannot get assistance because all lines are busy.
The last part of STRIDE is elevation of privilege, which concerns someone being able to accomplish a task they are not authorized to perform. With IS systems, an example would be a regular workstation user being able to install software as an administrator. Their permissions should be set to prevent this, but they may be able to gain access and do this. An easy example of elevation of privilege lies in the Linux operating system. Normally, a logged in user should not be able to perform administrative tasks. However, if the user is in the sudoer group, they can issue a command with sudo to elevate their permissions to that of the root user and perform a litany of tasks.
Threat modeling comes in various approaches. Shostack discusses the three primary approaches: asset, attack, and software. He provides good information on when these are best suited for use but ultimately makes the case for a software-centric approach as the best. Additionally, we have the STRIDE approach to threat modeling which appears to be a solid model with which to evaluate IS assets to ensure threats and vulnerabilities are accounted for. Whichever approach you use, it is always wise to think outside of the box to cover all possibilities and determine if the threat should be mitigated, eliminated, transferred, or accepted.
/cdn.vox-cdn.com/uploads/chorus_image/image/66596710/acastro_200331_1777_zoom_0003.0.0.jpg)